Sequoia Voting Systems
AVC Edge
Make / Model: Sequoia Voting Systems AVC Edge
Equipment Type: Direct Recording Electronic (DRE)
Summary

The Sequoia AVC Edge is a touch screen direct recording electronic voting machine. It is a multilingual voting system activated by a smart card and records votes on internal flash memory. Voters insert a smart card into the machine and then make their choices by touching an area on a computer screen, much in the same way that modern ATMs work. The votes are then recorded to internal electronic flash memory. When polls close, the votes for a particular machine are written to a PCMCIA card which is removed from the system and either physically transported to election headquarters or their contents transmitted via computer network.
The AVC Edge has a 15-inch LCD touchscreen that displays the ballot, allows voters to make selections and navigate the ballot, and provides an interface for testing, maintenance, and opening and closing the polls. On the front of each Edge unit is a slot for a smart card (also known as a “vote activation card”). A voter must have an activated smart card in order to begin voting. After the voter casts his or her ballot on the Edge, the smart card is deactivated and returned to a poll worker. This prevents one voter from voting multiple times.
The back of the Edge contains the power switch and a switch that opens and closes the polls on that particular voting machine. The cover for the poll function switch accommodates a tamper-evident seal. Also on the back of each Edge unit is a yellow “Activate” button, which can be used to switch the Edge into different operating modes. The backside of the Edge has a small LCD screen (two rows of 20 characters) that displays diagnostic and error messages. Sequoia uses a proprietary operating system for the Edge. Similarly, the firmware that the Edge uses to control the hardware and to allow voting are proprietary applications. The Edge also contains three serial EEPROMs (electronically programmable read-only memory), which store permanent configuration information about the Edge unit as well as ballot counters. One of these EEPROMs is the “configuration ROM,” which holds information to identify the machine and the customer and also contains a “cryptographic seed value.” The other EEPROMs hold a public counter (a counter that is reset at the beginning of each election) and a protective counter (a counter that is incremented each time a vote is cast and is never reset).
The ballot definition and audio files to assist visually impaired voters are programmed on a WinEDS election management system server and stored on the Results Cartridge. Prior to an election, the Results Cartridge is inserted into the Edge’s Results Port and covered by a plastic door, which is sealed with a tamper-evident seal. The Results Cartridge also stores the Audit Trail, which consists of ballot images, ballot summaries, and the event log. The Edge also stores a copy of the Audit Trail in the internal Audit Trail memory. If the Results Cartridge is lost, damaged, or destroyed, it can be recovered from this internal memory. Event logging for the Edge is always turned on; it cannot be disabled.
At the close of an election, a pollworker may print the audit log on a VVPAT. Alternatively, or additionally, election officials may access the event log stored as part of the Audit Trail on the Results Cartridge. Several other devices support the Edge. First, the Card Activator processes the smart cards (also known as “vote activation cards”) that voters use to access the Edge. After each use of a smart card, the Card Activator prepares the card for use by another voter. Before an election, each Card Activator must be prepared with the ballot definitions and other information appropriate for the precinct in which it will be used. An alternative to the Card Activator is the HAAT (Hybrid Activator, Accumulator, and Transmitter). There are two models of the HAAT, Model 50 and Model 100.
As of 2022, the AVC Edge is no longer used in U.S. elections.
Voting Process

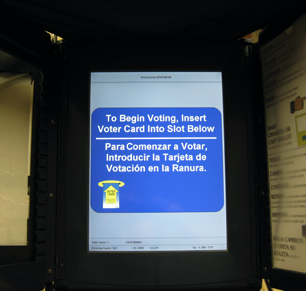
Activate Your Ballot A poll worker will give you a single-use “Voter Card.” Insert the card into the yellow slot on the Sequoia voting machine to activate your ballot. The card will remain in the machine until you have completed voting.
2. Vote When the list of choices appears on the screen, simply touch the box containing your preference. To change your selection, touch the box again. Touch the “Next” or “Back” arrows at the bottom of the screen to turn pages in your ballot.
3. Verify and Print After marking your ballot, a review screen allows you to see all of your selections. To make a change, touch the box you would like to revise and you will be returned to the corresponding page of the ballot. If the machine is fitted with a voter-verifiable paper audit trail (VVPAT), you will be asked to print and review a paper record of your ballot. The paper record will appear in the window on the left of the screen.
4. Cast Ballot After verifying the paper record, you may either touch the “Make Changes” or “Ballot” button on the screen. If you choose to make changes, a new paper record incorporating your revisions will be printed. When you select “Cast Ballot,” the printer will indicate the paper record was accepted by you, the voter. The paper and electronic record will remain securely stored inside the machine.
Checking the Voter-Verifiable Paper Trail: The Edge’s optional VVPAT printer is called the VeriVote. The VeriVote printer is a cash-register type printer and is located to the left of the touch screen. Jurisdictions that use the Edge but do not equip their machines with the VeriVote include the state of Louisiana.
Spurred by the testimony of computer scientists at a hearing in Santa Clara County, CA in January 2003, Sequoia Voting Systems was the first major vendor to produce a VVPAT retrot for their touch screen voting machine, the Sequoia AVC Edge. A team led by John Homewood led for a provisional application in the Spring of 2003 and a full patent application in early 2004. The Sequoia system uses a thermal printer and a roll of cash-register receipt tape. After each voter completes a ballot on the display screen, the printed choices are displayed behind a glass window for voter approval, and then rolled onto a take-up reel before the next voter enters the voting booth. Unlike the Avante Vote Trakker, the tape is not cut after each ballot is printed. The Premier/Diebold AccuView VVPAT mechanism and the Hart InterCivic VBO also use thermal paper.
When the polls close, a poll worker or election official inserts an administrator card into each voting machine and puts the machine into a postelection mode so it will no longer record votes. At this point, the machine writes the votes from its internal memory to flash memory on a PCMCIA card, a removable form of flash memory. A printed tape of all votes cast or vote totals for the voting machine can also be printed out at this time depending on local procedure and regulations. The PCMCIA cards are removed from each machine and either taken to a central tabulation facility or to remote tabulation facilities. At the tabulation facility the votes are copied from the PCMCIA cards into a central computer database where precincts are combined to result in an aggregate vote. The votes may also be transmitted to the central tabulation facility via a closed intranet, the Internet, or modem. The PCMCIA cards and any printouts from the voting machines can then become part of the official record of the election.
Voting Instructions:
1. Insert your Voter Access Card into the machine.
2. Select candidates by touching their names or the adjacent box; touch again to deselect. To vote for a write-in candidate, touch the Write-In line and a keyboard will appear. Type in the name of the candidate and touch the Record Write-In button to continue.
3. Use the Next and Back buttons to navigate if your ballot is more than one page.
4. Review your choices on the Summary screen, touch Cast Ballot to cast your vote.
5. Return your Voter Access Card to a precinct official when finished.
Video
A Voter Demo Edge without VVPAT from York County PA
Security Concerns
Researchers contracted by the California Secretary of State for the State’s Top to Bottom Review in 2007 found significant security weaknesses throughout the Sequoia system. The nature of these weaknesses raises serious questions as to whether the Sequoia software can be relied upon to protect the integrity of elections. Every software mechanism for transmitting election results and every software mechanism for updating software lacks reliable measures to detect or prevent tampering. These weaknesses and their implications are noted in Chapters 3 and 4 of the Source Code Report.
In certain cases, audit mechanisms may be able to detect and recover from some attacks, depending on county-specific procedures; other attacks may be more difficult to detect after the fact, even with very rigorous audits. There were numerous programming, logic, and architectural errors present in the software reviewed. Some of these errors may be relatively harmless and reflect the large size and heterogeneous nature of the codebase. Other errors found have serious security implications. Many of the most significant vulnerabilities found — those likely to be especially useful to an attacker seeking to alter election results — arise from four pervasive structural weaknesses:
Data Integrity The Sequoia system lacks effective safeguards against corrupted or malicious data injected onto removable media, especially for devices entrusted to poll workers and other temporary staff with limited authority. This lack of input validation has potentially serious consequences, including the following:
- Precinct election results stored on DRE Results Cartridges and optical scan memory packs are not effectively protected against tampering. A poll worker with physical access to a Results Cartridge or MemoryPack before results are counted (e.g. when returning results to the county elections board) can change recorded votes, and, in some cases, can introduce spurious results for other precincts. Under some conditions, a corrupted Results Cartridge may be able to cause damage to the WinEDS system itself when it is loaded for vote counting.
- The safeguards against introduction of corrupt firmware into the precinct voting hardware are largely ineffective. An individual with even brief access to polling station hardware can tamper with installed firmware in a way that causes votes and paper trails to be recorded incorrectly, security logs to be corrupted, or ballots to be presented to voters incorrectly. Under some configurations and conditions, corrupt firmware may be able to be spread virally from compromised hardware and may persist across more than one election.
Cryptography Many of the security features of the Sequoia system, particularly those that protect the integrity of precinct results, employ cryptography. Unfortunately, in every case examined, the cryptography is easily circumvented. Many cryptographic functions are implemented incorrectly, based on weak algorithms with known flaws, or used in an ineffective or insecure manner. Of particular concern is the fact that virtually all cryptographic key material is permanently hardcoded in the system (and is apparently identical in all Sequoia hardware shipped to different jurisdictions). This means that an individual who gains temporary access to similar hardware (inside California or elsewhere) can extract and obtain the secret cryptographic keys that protect elections in every jurisdiction that uses the system.
Access Control The access control and other computer security mechanisms that protect against unauthorized use of central vote counting computers and polling place equipment are easily circumvented. In particular, the security features and audit logs in the WinEDS back end system (used for ballot preparation, voting machine configuration, absentee ballot processing, and post-election vote counting) are largely ineffective against tampering by insider attackers who gain access to WinEDS computers or to the network to which the WinEDS computers are attached.
Software Engineering The software suffers from numerous programming errors, many of which have a high potential to introduce or exacerbate security weaknesses. These include buffer overflows, format string vulnerabilities, and type mismatch errors. In general, the software does not reflect defensive software engineering practices normally associated with high-assurance critical systems. There are many instances of poor or absent error and exception handling, and several cases in which the software behavior does not match the comments and documentation. Some of these problems lead to potentially exploitable vulnerabilities that were identified, but even where there may not be an obvious vulnerability identified, the presence of such errors reduces our overall confidence in the soundness of the system as a whole.
References
New Jersey Institute of Technology Report (2007)
Security Evaluation of the Sequoia Voting System Public Report, Computer Security Group, Department of Computer Science, University of California, Santa Barbara (2008)
New Jersey Institute of Technology AVC Edge Report (2007)
“DRE Security Assessment, Volume 1, Computerized Voting Systems, Summary of Findings and Recommendations,” InfoSENTRY (Nov. 21, 2003)
Manufacturer Profile

Sequoia Voting Systems (now owned by Dominion Voting Systems)
1800 Glenarm Place, Suite 500
Denver, CO 80202
(866) 654-VOTE (8683)
Sequoia was involved with voting systems for more than 100 years. At the end of the 19th century, Sequoia invented the lever-action mechanical voting system. Many machines of this type are still used today in some U.S. jurisdictions. In the 1980s Sequoia was bought by Jefferson Smurfit, an Irish printing conglomerate which in turn sold it to De La Rue, a British currency paper printing and security company. After losing money for several years, on March 8, 2005, Sequoia was acquired by Smartmatic, a multi-national technology company which had developed advanced election systems, voting machines included. In November 2007, following a verdict by the CFIUS, Smartmatic was ordered to sell Sequoia, which it did to its Sequoia managers with U.S. citizenship. Sequoia Voting Systems was acquired by Denver-based Dominion Voting Systems on June 4, 2010.